Difference between revisions of "Home Automation"
(→Servo Controlled) |
Bendersgame (Talk | contribs) m (→Edits to Flowchart: typo) |
||
| (7 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
| − | = | + | =Roadmap= |
* Pick an authentication method '''DONE''' USB | * Pick an authentication method '''DONE''' USB | ||
| − | * Computer driven scripts to send signal to USB | + | * Computer driven scripts to send signal to USB '''DONE''' |
** read in USB info '''DONE''' | ** read in USB info '''DONE''' | ||
| − | ** send out serial command | + | ** send out serial command '''DONE''' |
| − | * Pick an physical entry method | + | * Pick an physical entry method '''DONE''' |
| − | * Use serial command to trigger entry method | + | * Use serial command to trigger entry method '''DONE''' |
| + | * Attach everything to the door '''DONE''' | ||
=Entry Automation= | =Entry Automation= | ||
| Line 23: | Line 24: | ||
===Cons=== | ===Cons=== | ||
* Keys easily stolen with anonymity | * Keys easily stolen with anonymity | ||
| − | |||
===Implementation=== | ===Implementation=== | ||
====Materials==== | ====Materials==== | ||
| − | * Need a reader | + | * Need a reader. Can be found for [http://cgi.ebay.com/ws/eBayISAPI.dll?ViewItem&item=300060435830&ssPageName=MERC_VI_RSCC_Pr12_PcY_BIN_Stores_IT&refitem=300222598671&itemcount=12&refwidgetloc=active_view_item&usedrule1=StoreCatToStoreCat&refwidgettype=cross_promot_widget&_trksid=p284.m184&_trkparms=algo%3DDR%26its%3DS%252BI%252BSS%26itu%3DISS%252BUCI%252BSI%26otn%3D12 under $100] |
| − | + | * Need tags | |
| − | * Need | + | |
| − | + | ||
* Need a server | * Need a server | ||
| Line 36: | Line 34: | ||
===Pros=== | ===Pros=== | ||
* Rotating keys are available | * Rotating keys are available | ||
| − | * | + | * Physical access is required for key duplication |
===Cons=== | ===Cons=== | ||
* Hands-on access | * Hands-on access | ||
| − | * | + | * Interface may be fakable with any interface that has the same signal levels [[iButton Spoofing]] --[[User:Omegix|Omegix]] 23:02, 8 May 2008 (CDT) |
| − | + | ** Unimportant, because the threat of theft through kicking the door in is much higher than spoofing --[[User:Korc|Korc]] 20:51, 8 May 2008 (CDT) | |
| − | + | ||
| − | ** | + | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
==USB Authentication== | ==USB Authentication== | ||
===Pros=== | ===Pros=== | ||
| Line 92: | Line 81: | ||
to not only receive a signal from the computer, but also sense a window-open detector, and control a servo. | to not only receive a signal from the computer, but also sense a window-open detector, and control a servo. | ||
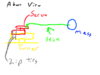
| − | This sketch from Feltinix shows how a stick hanging from the servo could be used to | + | This sketch from Feltinix shows how a stick hanging from the servo casing could be used to action / reaction hold the servo in place. |
| + | |||
| + | If you were to attach the stick to the deadbolt turner or the plastic connected to the servo motor shaft, that would allow for a manual unlocker for the door in the event of a power failure | ||
[[Image:Tanstaafl%27slockproposal.png|thumb|none|100px|10/04/2008]] | [[Image:Tanstaafl%27slockproposal.png|thumb|none|100px|10/04/2008]] | ||
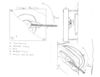
| + | This image from gregabyte shows a mechanical override system that could be implemented for under $20 | ||
| − | + | [[Image:Img-X08155151-0001.jpg|thumb|none|100px|10/04/2008]] | |
| + | |||
| + | |||
| + | The flowchart for the circuit is below. | ||
[[Image:ServoControlled.jpg|thumb|none|100px|10/04/2008]] | [[Image:ServoControlled.jpg|thumb|none|100px|10/04/2008]] | ||
| Line 103: | Line 98: | ||
=====Edits to Flowchart===== | =====Edits to Flowchart===== | ||
# Sound a buzzer right before the door unlocks or locks so that users are aware that something is about to happen | # Sound a buzzer right before the door unlocks or locks so that users are aware that something is about to happen | ||
| + | |||
| + | |||
| + | [[Category:Arduino]] | ||
Latest revision as of 15:37, 4 March 2010
Contents
[hide]Roadmap
- Pick an authentication method DONE USB
- Computer driven scripts to send signal to USB DONE
- read in USB info DONE
- send out serial command DONE
- Pick an physical entry method DONE
- Use serial command to trigger entry method DONE
- Attach everything to the door DONE
Entry Automation
General Implementation Notes
- The system needs to be powered, and preferably include a UPS
- Overriding key access is nice for graceful failure
- Of course, this just underlines the fact that this is an access registry system more than anything
- Probably need a normal handle in the door with an electric door strike for the cheapest implementation.
- If the implementation simply replaces the metal key with a token, it will have the same problems. Unless two- or three-factor authentication is used and/or the physical security of the lock and door are improved, it's about as secure as it was.
- Simple enough to manage the coming and going of people.
RFID
Pros
- Hands-off access
- Hands-off tracking of access
- As long as user has their RFID tag on them, their presence within a certain proximity around the reader will be recorded.
Cons
- Keys easily stolen with anonymity
Implementation
Materials
- Need a reader. Can be found for under $100
- Need tags
- Need a server
iButton
Pros
- Rotating keys are available
- Physical access is required for key duplication
Cons
- Hands-on access
- Interface may be fakable with any interface that has the same signal levels iButton Spoofing --Omegix 23:02, 8 May 2008 (CDT)
- Unimportant, because the threat of theft through kicking the door in is much higher than spoofing --Korc 20:51, 8 May 2008 (CDT)
USB Authentication
Pros
Each USB device has a unique serial ID. USB keys are cheap, readily available, and many can fit on a standard metal keyring.
Cons
Implementation
Authentication Flow
- User inserts key into USB hub hooked to a PC
- Computer reads serial ID of key
- Computer compares serial ID to list of valid serial ID in a table \ DB \ Flat File
- If good, computer writes data ("Unlock!") to USB line of Microcontroller
- Microcontroller throws a pin high for 5-10 seconds.
- Pin is likely 3-5volts. Pin is wired to either a 200ma transistor or relay
- Relay, when thrown, sends 12V of 200mA current to an electric doorstrike
Useful Microcontroller (Arduino/Freeduino) Resources
Suggested Implementation Phases
- Get microcontroller to throw a pin high
- Get microntroller to read commands issued from external system (serial/USB)
- Get microcontroller to throw Pin high after recieving external command
- Build and test simple door strike circuit
Circuit
In order to get 12V of 200mA current to the doorstrike, we'll need to protect the freeduino from flyback current. After consulting with protomech, 1kOhm resistor, one 1N4002 diode, and one 2N2222 transistor should do the trick for making a safe 12V relay for the doorstrike.
Other Materials
- Door Strike, Normally Open (NO) Normally Open means that it doesn't require power to stay locked.
Mechanical Implementation
DoorStrike
Electric Deadbolt
- This Guide Shows how to easily hack a Powerbolt 1000.
- Cost is roughly $80
Servo Controlled
The idea here is to have a servo attached to a standard deadbolt. The microcontroller will need to not only receive a signal from the computer, but also sense a window-open detector, and control a servo.
This sketch from Feltinix shows how a stick hanging from the servo casing could be used to action / reaction hold the servo in place.
If you were to attach the stick to the deadbolt turner or the plastic connected to the servo motor shaft, that would allow for a manual unlocker for the door in the event of a power failure
This image from gregabyte shows a mechanical override system that could be implemented for under $20
The flowchart for the circuit is below.
Edits to Flowchart
- Sound a buzzer right before the door unlocks or locks so that users are aware that something is about to happen